Office 365 Incoming Mail not populating due to Malicious Rule
We recently had a client who opened a spam email and it sent spam to all of their internal contacts. His profile got corrupted so our onsite tech recreated it but now the client can only send out emails and cannot receive any emails—internal or external. I’m waiting for Office 365 admin credentials (They All changed their passwords from the scare and admin did as well) to dig deeper but does anyone know if Microsoft has a built in feature that would kill his incoming mail after this spam fiasco?
We verified the MX Lookup comes back correct in that it’s pointing to the Office 365 mail servers and not another third party filter. We also verified senders were not getting any bounces or non-delivery reports when attempting to send to his address.
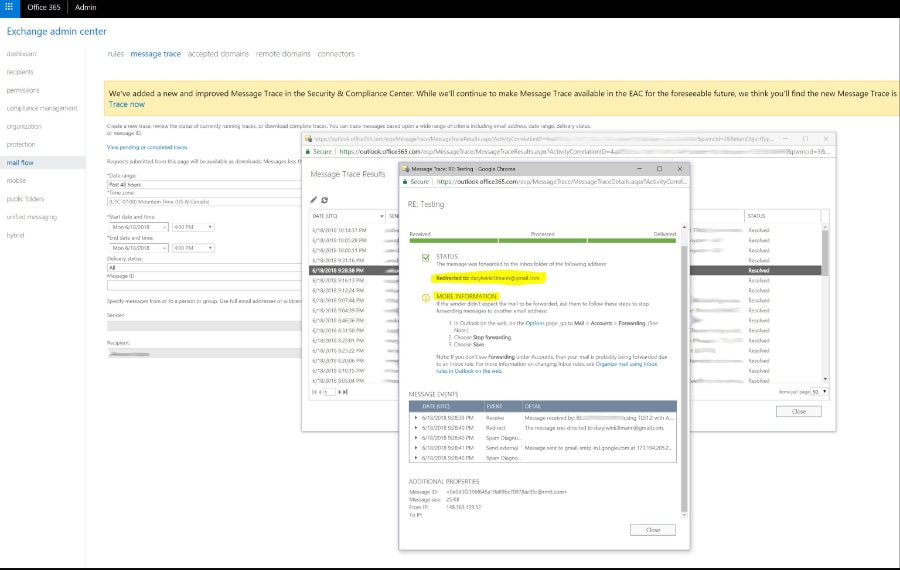
After logging into the Exchange admin center with Office 365 with administrator credentials, we used the Message Trace tool in the Security & Compliance section to investigate further.
As it turned out, when the client opened the malicious email it created a local mail rule to forward all mail to a different address.
We could not see this rule in Mail Flow of Exchange Control Console. Below is a screenshot to show the forward in place without listing it in Mail Flow itself. Tricky situation.