pfSense – Isolate vLANs with an Interface Group
The Use Case
One pfSense with multiple vLANs that need to be locked down or isolated from each other. Also, need to block many vLANs from being able to access the pfSense web interface. For example, an environment where you host servers for different clients
The Theory
Firewall rules are process in this order: Floating>Interface Group>Interface. Create a Floating rule to allow pfSense access to the LANs/Devices that should be allowed to access the pfSense web interface. Create a Interface Group rules that allows LANs/Devices to talk to pfSense for DNS (if needed), blocks all other traffic to pfSense, blocks traffice to RFC1918 addresses (via Alias). LAN Interfaces can have default allow rule.
The How-To
Create Aliases
I created two aliases to make this work:
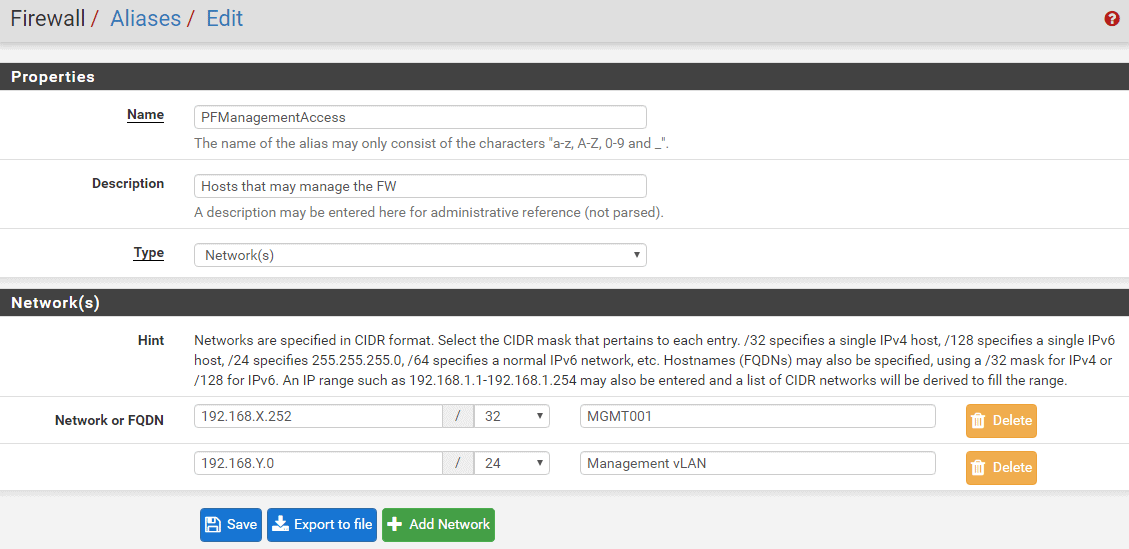
- PFManagmentAccess: list of all IPs/LANs that should have access to the pfSense (replace X and Y with your subnet)
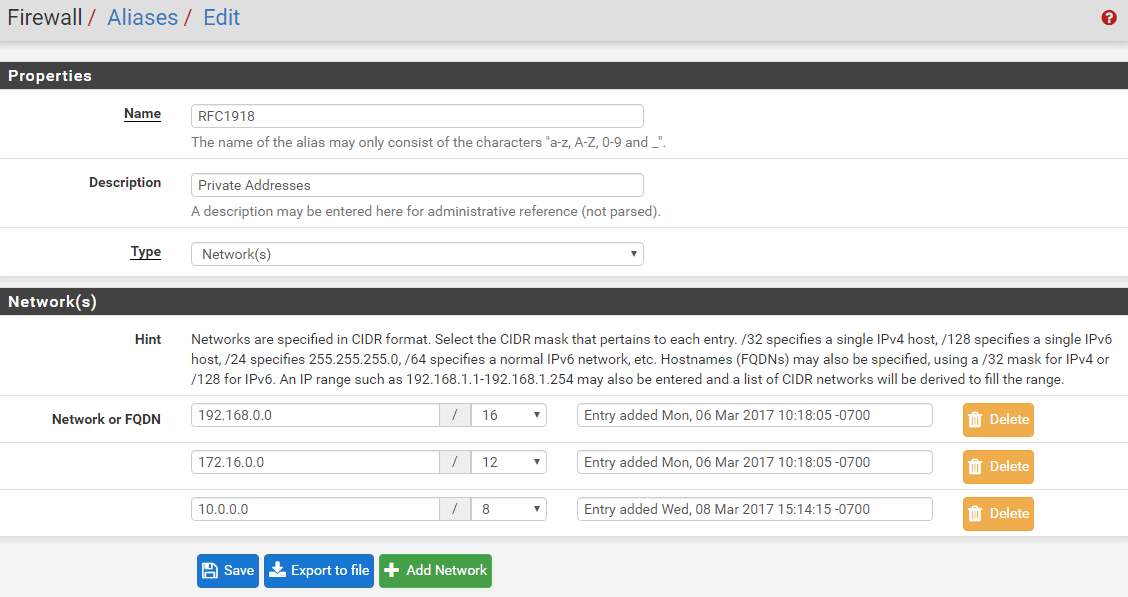
- RFC1918: all class C IP addresses. Add 192.168.0.0/16, 172.16.0.0/12, 10.0.0.0/8
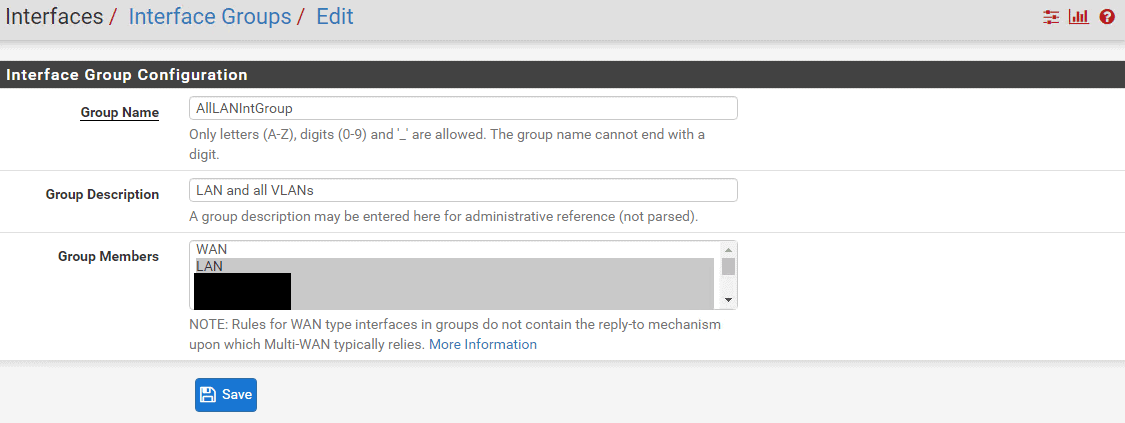
Create an Interface Group
- Interfaces>Assignments>Interface Groups>Add. Name Group and add all Interfaces that you want isolated. Do not select WAN.
- As you add more vLANs later on, this is the only spot you’ll need to add the new vLAN to
Create the Rules
Floating Rule
- Quick: Yes
- Source: Single host or alias – PFManagementAccess (alias you created above)
- Destination: This Firewall (self)
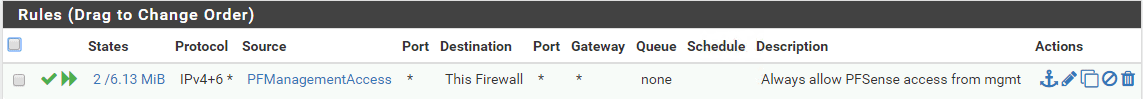
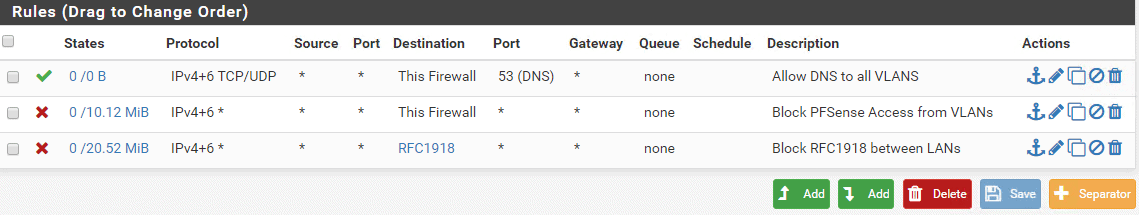
Interface Group Rules (top to bottom order)
Allow DNS access to pfSense
- Action: Allow
- Protocol: TCP/UDP
- Source: any
- Destination: This firewall (self)
- Destination Port Range: DNS (53) to DNS(53)
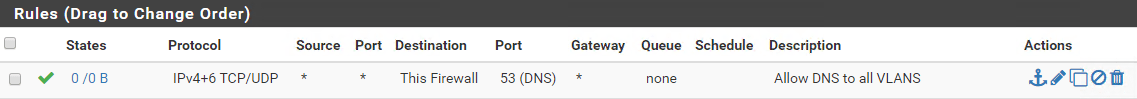
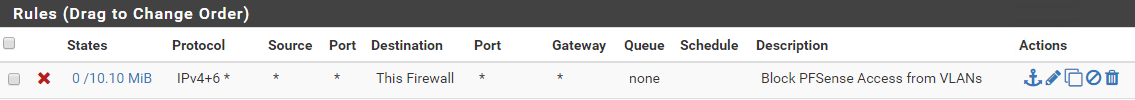
Block all other traffic to pfSense
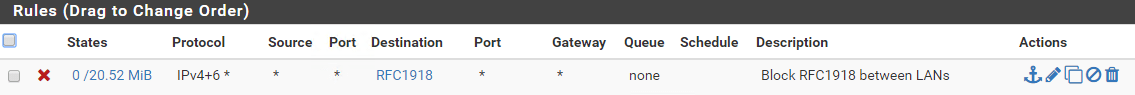
Block all traffic between vLANs
- Action: Block
- Protocol: Any
- Source: Any
- Destination: Single host or alias: RFC1918 (alias you created above)