N-Central – LDAP Integration and Troubleshooting
To integrate Active Directory (LDAP) Users into N-Central:
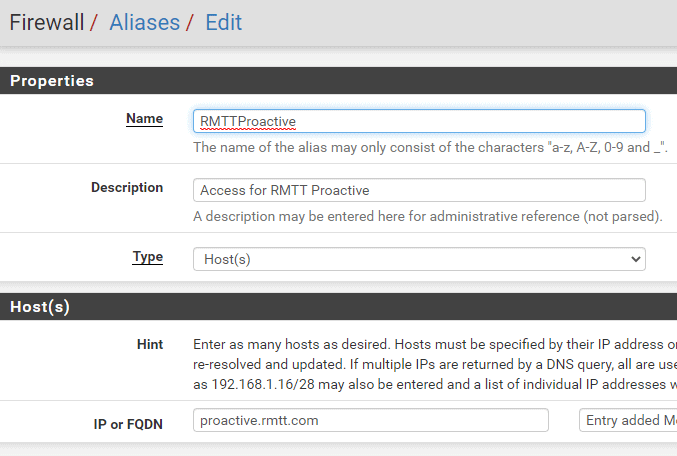
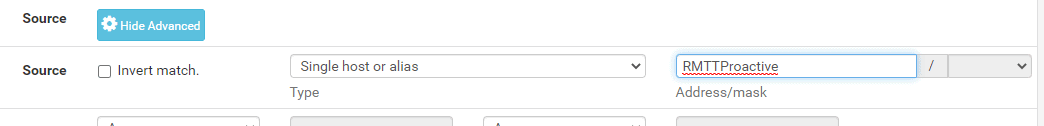
- Forward port 389 through the customer firewall to their domain controller (restrict the source to proactive.rmtt.com & set to fwd any port)
- Navigate to Customer Level at proactive.rmtt.com (top left will be green with customer’s name)
- Click Administration > User Management > SSO Providers
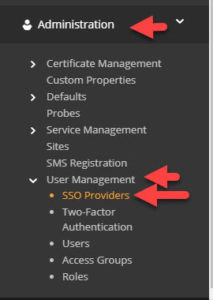
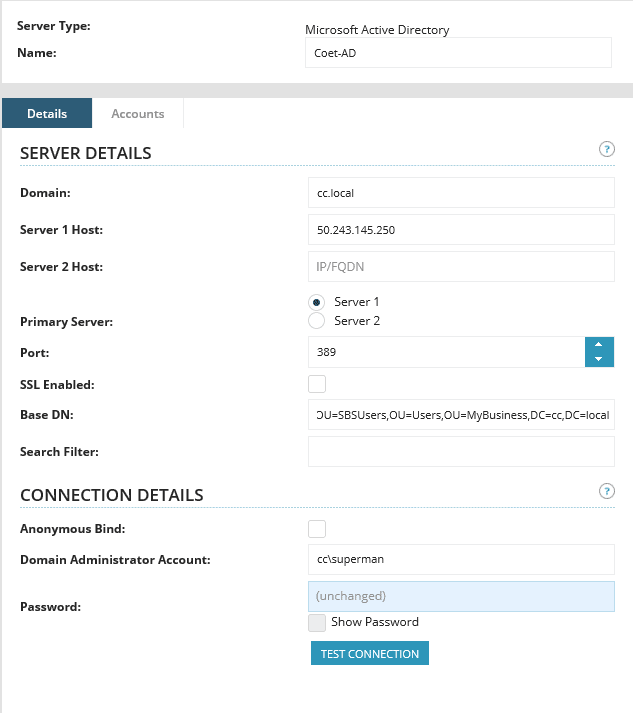
- Add > Microsoft Active Directory and fill out server details
- Under Name, type customer name-AD (ex: Coet-AD)
- Domain = domain name
- Server 1: Public IP or Public FQDN
- Base DN is easiest found using dsquery on the customer server. Make sure you use a user account in the same organizational unit as all the other user accounts. Leave out CN=username (in this example superman), so the entry would be OU=SBSUsers,OU=Users,OU=MyBusiness,DC=cc,DC=local

- Enter Domain Admin creds and select Test Connection. If DA creds change often, create another domain admin account for this item or you will need to change password here anytime it’s changed on server side.
TROUBLESHOOTING
If you change the domain admin creds that are tied to the user account you bind to LDAP with, you will need to follow these steps:
- Change password under Admin > User Management > SSO Providers, hit Test/Save
- Go to SO Level (for RMTT users)/Customer Level for individual clients and then click User Accounts
- Select All, then click Unlock
- Users should be able to login again